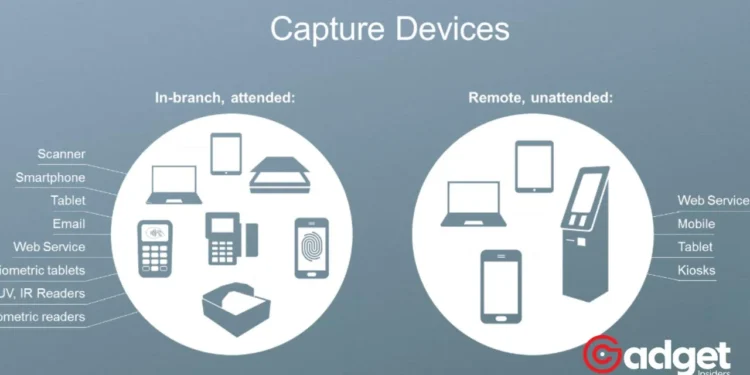
In an era where digital security is paramount, the initiative dubbed “Project Verify” emerges as a beacon of innovation, aiming to redefine how we manage our digital identities. Spearheaded by the titans of telecommunications—AT&T, Verizon Wireless, T-Mobile US, and Sprint—Project Verify promises a seamless and secure way to authenticate user identities across a myriad of third-party websites and applications.
A Unified Front Against Cyber Insecurity
The collaboration between these telecom giants marks a significant step forward in tackling the ever-evolving challenges of digital security. By leveraging a multi-factor authentication system, Project Verify aims to minimize the cumbersome process of password entries, thereby enhancing the user experience while bolstering security measures.
Telecom: The Mechanics of Project Verify
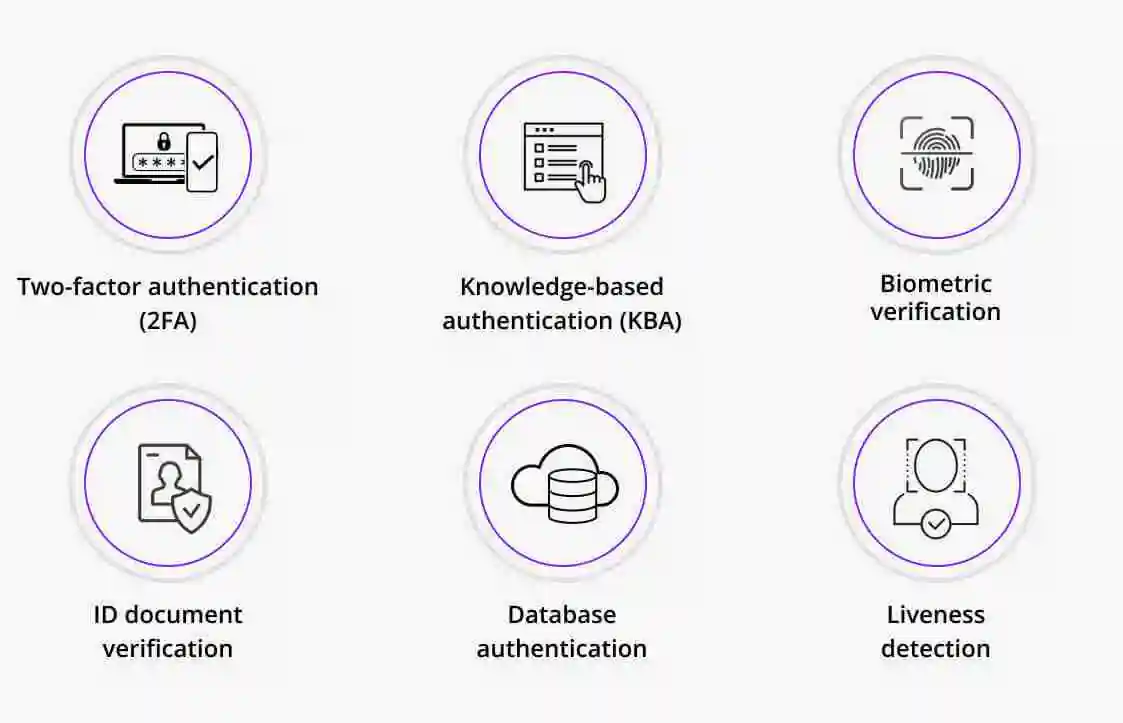
At its core, the Project of the telecom giants Verify and operates by allowing users to approve or deny login requests via their mobile devices. This system integrates various factors such as phone number, account tenure, IP address, and SIM card details to create a robust profile for each user.
By doing so, it offers a more nuanced and secure method of identity verification compared to traditional single-factor authentication methods.
The Convenience of Seamless Authentication
Imagine logging into your favorite apps and websites without the hassle of remembering countless passwords. With Project Verify from the telecom giants, this convenience is no longer a mere aspiration but a tangible reality. Users can simply select the verify option on login screens, entrusting Project Verify to handle the rest.
In 30 mins, #ZenKey will be participating at the #identity seminar to explain how @ATT, @sprint, @TMobile and @verizon have joined forces to protect their subscribers' digital identity. Come and join us in Concourse Hall, room 408B.https://t.co/iRf7A9XDqq pic.twitter.com/OHFydT43e8
— GSMA Events (@GSMAEvents) October 22, 2019
A Call to Developers
The Telecom companies and the consortium behind Project Verify extend an invitation to developers of third-party apps and websites, encouraging them to integrate this innovative authentication system. This collaboration aims to create a more secure and user-friendly digital ecosystem, paving the way for widespread adoption.
Security Concerns and Skepticism
A discussion over privacy and security has been sparked as a result of the suggestion made by telecom carriers to control our digital logins. This is even though the benefits are promising.
The transgressions that the carriers have committed in the past, such as the unauthorized sale of location data, are cited as warning signs by critics, who question whether or not it is possible to entrust them with even more sensitive information.
Security experts express skepticism about the carriers’ ability to securely manage logins, citing the prevalence of SIM swap scams and mobile number port-out frauds as indicators of their current security shortcomings. The apprehension revolves around the potential for Project Verify to make mobile phones a more attractive target for cybercriminals.
Upholding Data Privacy
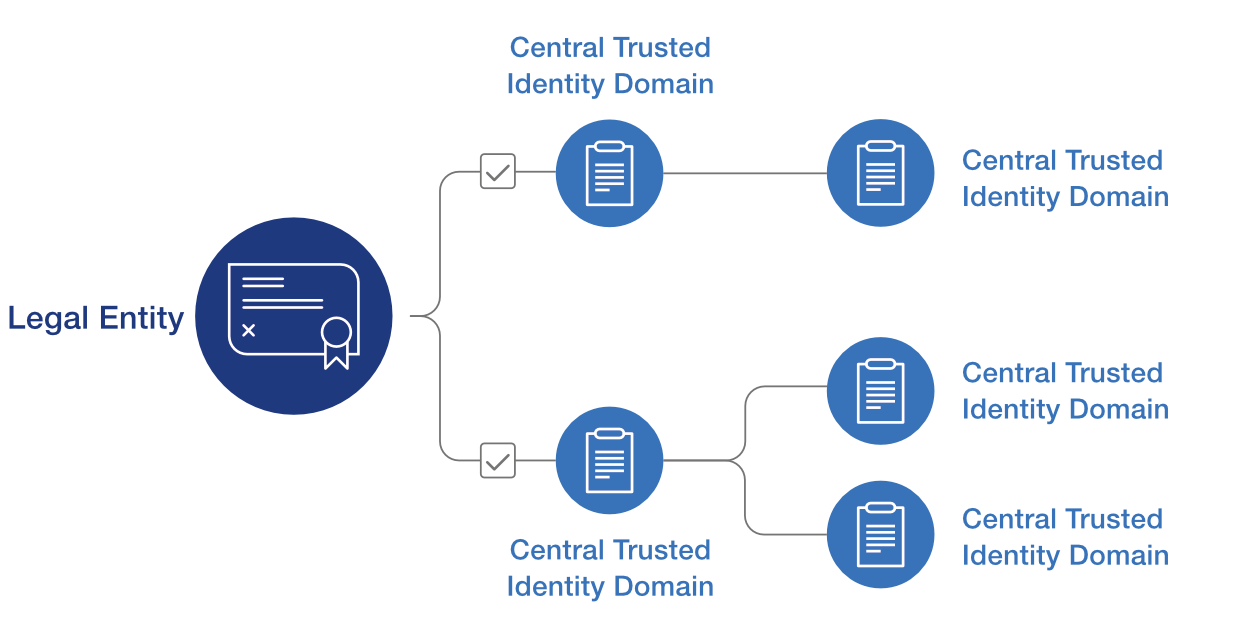
In response to these concerns, Johannes Jaskolski, the AT&T VP overseeing Project Verify, assures that subscriber data will not be centralized into a multi-carrier database. Instead, each carrier will maintain separate control over its data, with a design that prioritizes portability and user control over third-party data sharing.
The Path Forward
As Project Verify prepares for its launch, the telecommunications industry stands at a pivotal crossroads. The initiative represents a groundbreaking effort to enhance digital security, but it also highlights the critical need for trust and transparency between service providers and their customers.
The success of Project Verify will ultimately depend on its ability to balance convenience with security, all while navigating the complex landscape of digital privacy concerns. As we inch closer to its implementation, the digital community watches with bated breath, hopeful for a future where digital identities are both easily manageable and securely protected.