In a significant pivot from its earlier iteration, Microsoft’s Recall feature for Copilot+ Windows PCs is undergoing a comprehensive security overhaul. The tech giant’s initial launch plan hit a snag following intense scrutiny over privacy concerns and security vulnerabilities. However, in a recent detailed announcement by David Weston, Microsoft’s VP of Enterprise and OS Security, the company unveiled its plans to re-introduce Recall with robust security measures and enhanced user control options.
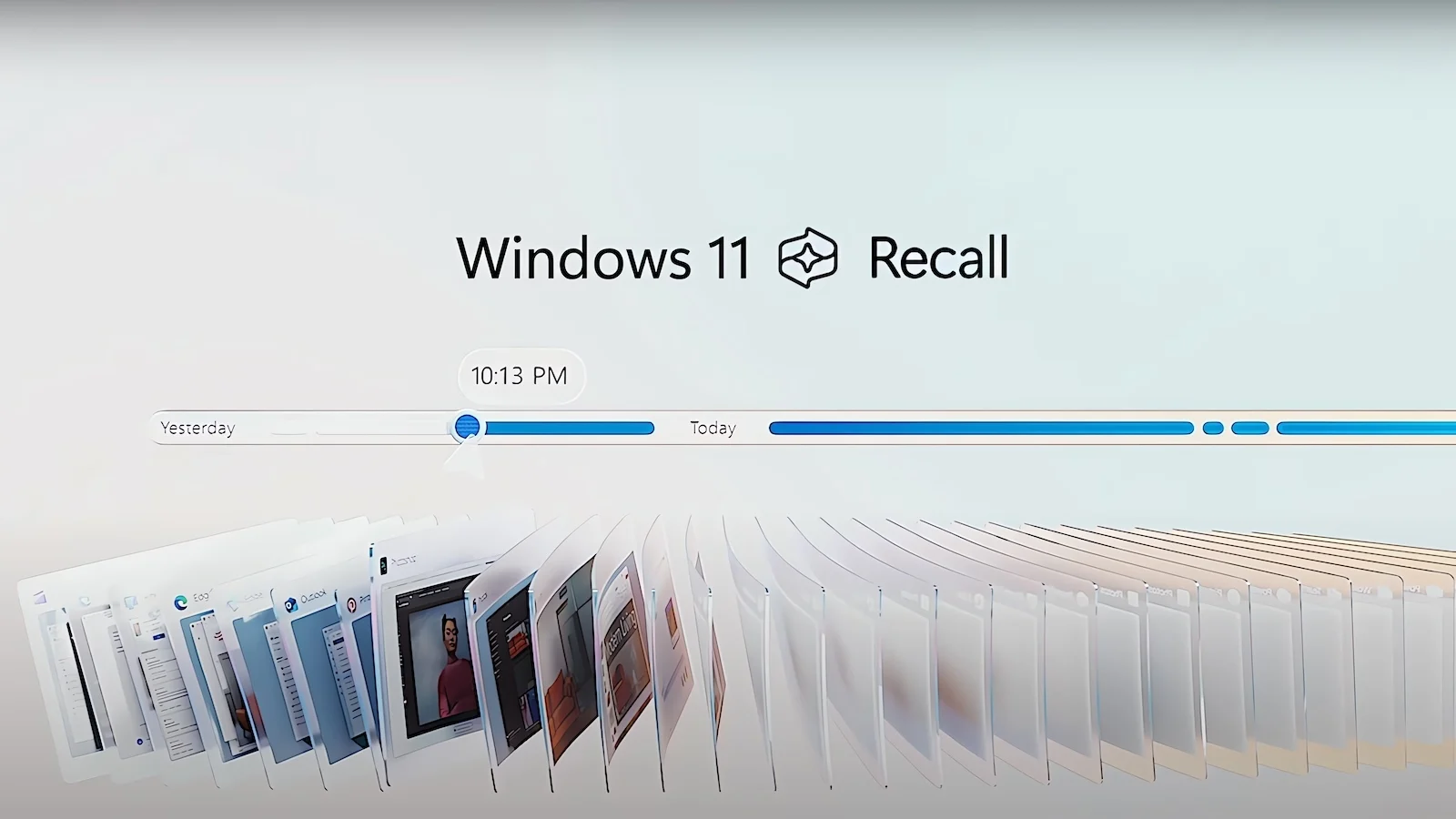
Rethinking Security: The New Architecture of Recall
Originally criticized for its invasive data collection methods, which included unencrypted storage of user data on local disks, the revamped Recall promises a stark contrast. In response to the backlash, Microsoft has redesigned Recall’s security architecture, ensuring that the feature is now optional and off by default, a shift from the previously critiqued opt-out approach.
The new security framework introduces several key enhancements aimed at safeguarding user privacy:
- Encryption at Rest: All local Recall data, including snapshots and associated information in the vector database, will now be encrypted with keys stored securely in the system’s TPM (Trusted Platform Module).
- Mandatory Security Features: Recall’s operation is contingent on the activation of BitLocker or Device Encryption. Furthermore, it requires Virtualization-Based Security (VBS) and Hypervisor-Protected Code Integrity (HVCI), which must be enabled for Recall to function effectively.
- Isolated Data Protection: Leveraging VBS enclaves, Recall ensures that all data is isolated within a secure memory segment that can only be accessed post-authentication via Windows Hello. This setup provides a robust isolation boundary protecting against both kernel and administrative intrusions.
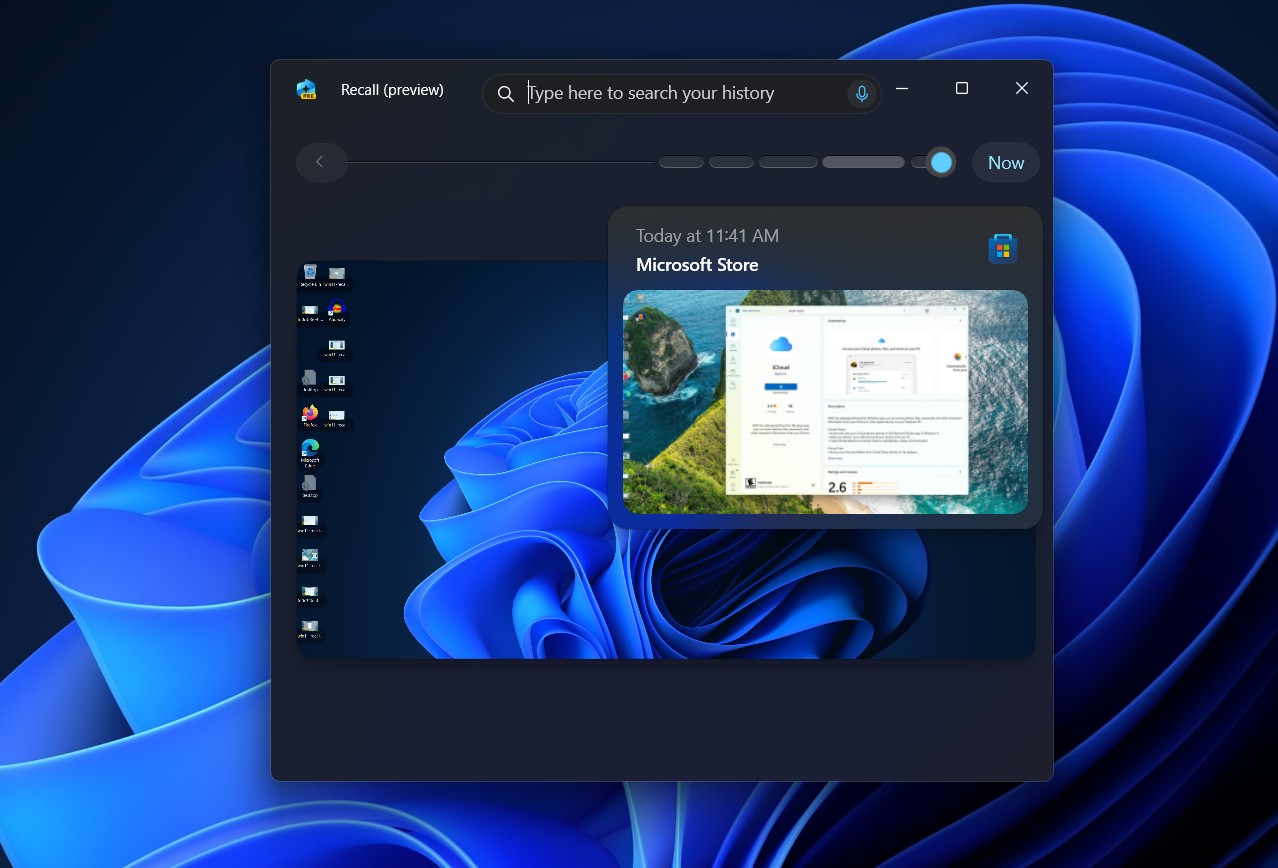
User Empowerment and Flexibility
Addressing one of the major concerns from its initial release, Microsoft has made Recall completely removable from the system. Users can now eliminate the feature entirely via the “optional features” settings in Windows, ensuring that those who prefer not to use the tool can easily opt-out without compromising their system’s functionality. This change comes after an incident earlier in the month when a similar removal option appeared in a Windows preview and was mistakenly reported as a bug by Microsoft. The company has since confirmed that this functionality is intentional and reflects its renewed commitment to user control and transparency.
Strengthening Defenses Against Malware
In addition to structural security improvements, Microsoft is implementing new malware protection strategies within Recall. These include rate-limiting and anti-hammering measures to prevent malicious attempts to access or exploit user data. By only allowing code signed by Microsoft to run within the VBS enclaves, Recall significantly reduces the risk of malware interference, ensuring that user data remains secure from unauthorized access.
Microsoft’s overhaul of the Recall feature signifies a crucial step forward in addressing the privacy and security concerns that have plagued its initial release. With a focus on encryption, optional participation, and comprehensive malware protection, Microsoft aims to restore trust and offer a more secure, user-friendly experience. As Recall prepares for its re-launch, it exemplifies Microsoft’s responsiveness to user feedback and its commitment to upholding high standards of data protection and privacy within its operating systems.










